Inside this article :
What if you could slash your cloud infrastructure costs in half while actually improving security and developer productivity?
That’s exactly what leading companies like Spotify, Airbnb, and dozens of our enterprise clients have achieved through strategic Kubernetes multi-tenancy implementation. Instead of managing hundreds of isolated clusters each burning through compute resources at 20% utilization they’ve consolidated workloads onto shared infrastructure that runs at 80%+ efficiency without sacrificing isolation or performance.
The stakes couldn’t be higher. With cloud costs spiraling out of control and DevOps teams stretched thin managing endless clusters, organizations face a critical decision: continue bleeding money on underutilized infrastructure, or master the art of secure multi-tenancy to unlock unprecedented efficiency gains.
In this comprehensive guide, we’ll reveal the exact strategies, security patterns, and implementation frameworks that have helped our clients reduce infrastructure costs by 40-60% while accelerating developer velocity and strengthening their security posture. Whether you’re a platform architect drowning in cluster sprawl or a SaaS founder seeking cost-effective scalability, this guide contains the battle-tested insights you need to transform your Kubernetes strategy.
What is Kubernetes Multi-Tenancy? A Deep Dive
Kubernetes multi-tenancy refers to the practice of running multiple isolated workloads, users, or applications on a shared Kubernetes cluster. Think of it as a well-designed office building where different companies occupy separate floors, sharing common infrastructure like elevators and utilities while maintaining complete privacy and security boundaries.
This architectural pattern has become essential for organizations looking to:
- Reduce infrastructure costs by consolidating workloads
- Streamline operations through centralized cluster management
- Accelerate development with faster environment provisioning
- Improve resource utilization across teams and projects
The Business Case for Multi-Tenant Kubernetes
Modern enterprises face mounting pressure to do more with less. Traditional approaches of provisioning dedicated clusters for each team or application quickly become expensive and operationally complex. Multi-tenancy addresses these challenges by:
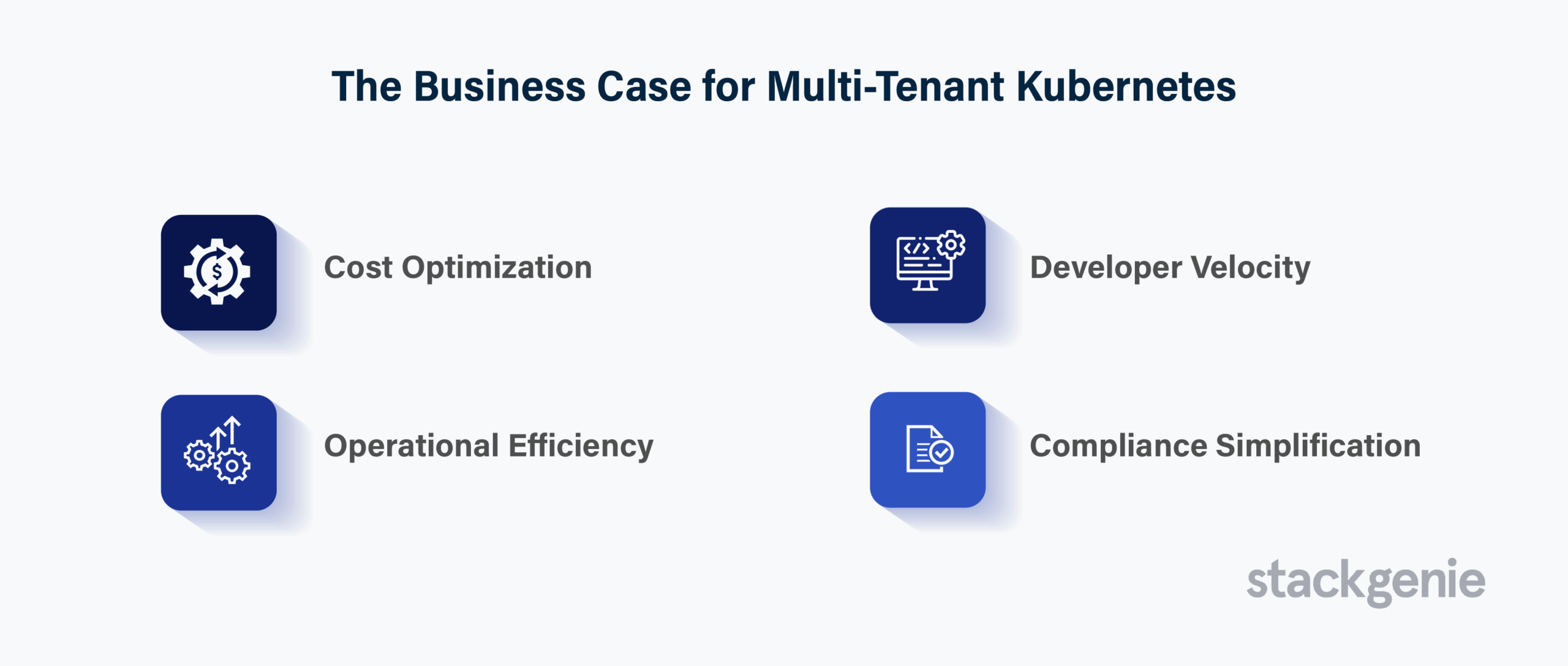 Cost Optimization: Shared infrastructure reduces hardware, licensing, and operational expenses by 40-60% compared to dedicated cluster approaches.
Cost Optimization: Shared infrastructure reduces hardware, licensing, and operational expenses by 40-60% compared to dedicated cluster approaches.
Operational Efficiency: Platform teams can manage hundreds of applications from a single control plane, dramatically reducing administrative overhead.
Developer Velocity: New teams can be onboarded in minutes rather than weeks, accelerating time-to-market for new products and features.
Compliance Simplification: Centralized policy enforcement ensures consistent security postures and regulatory compliance across all tenants.
Multi-Tenancy Models in Kubernetes: Choosing the Right Approach
Kubernetes doesn’t provide built-in multi-tenancy capabilities, but several proven patterns have emerged. Each model offers different trade-offs between isolation, cost, and operational complexity.
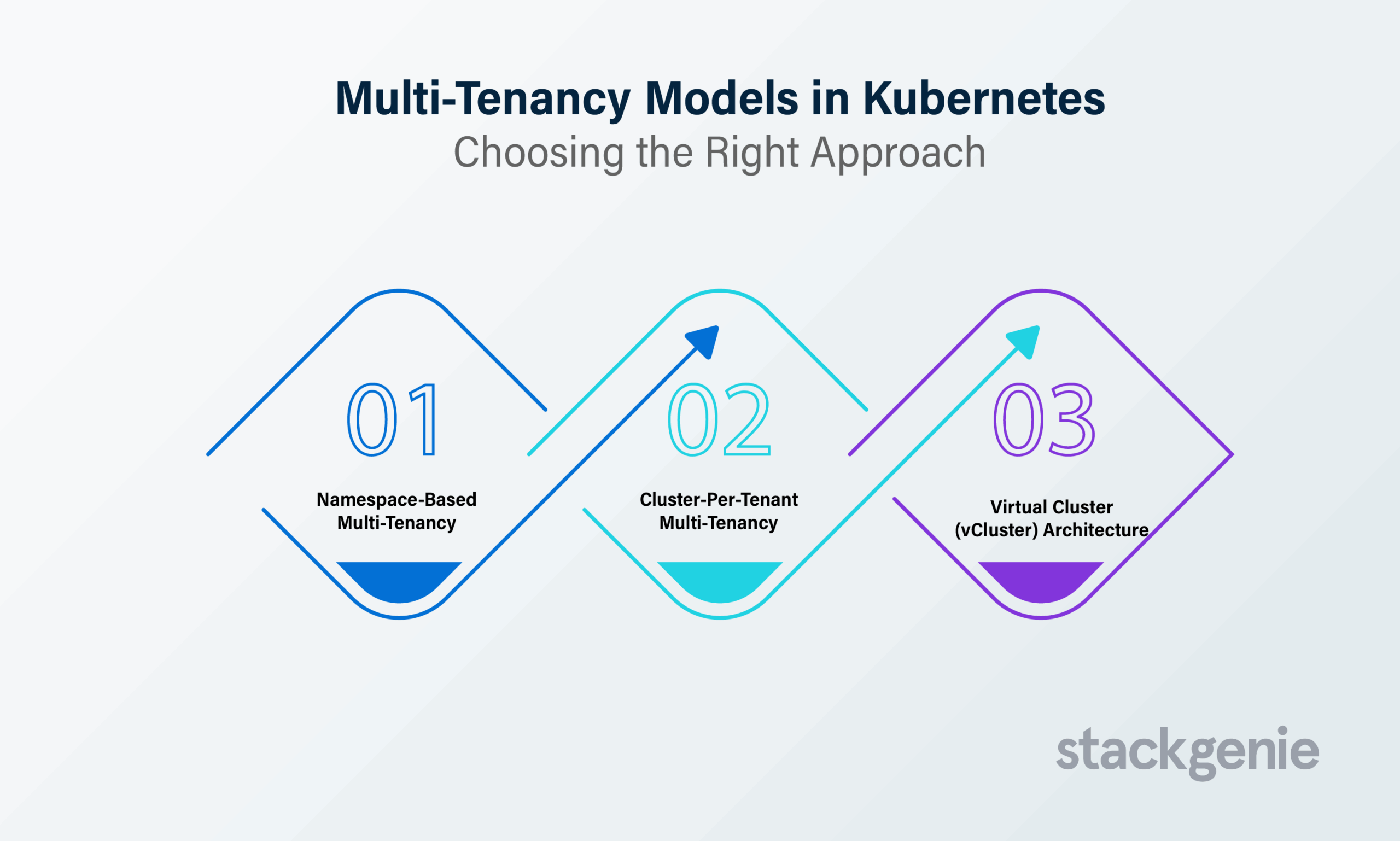 1. Namespace-Based Multi-Tenancy
1. Namespace-Based Multi-Tenancy
The most widely adopted approach, namespace-based multi-tenancy assigns each tenant their own Kubernetes namespace with strict RBAC controls.
Implementation Benefits:
- Minimal setup complexity and fast deployment
- Native Kubernetes resource management
- Excellent tool ecosystem compatibility
- Low resource overhead
Security Considerations:
- Shared control plane requires robust RBAC configuration
- Network-level isolation needs careful NetworkPolicy design
- Node-level isolation may require additional tooling
Best For: Development environments, internal teams, and organizations with moderate security requirements.
2. Cluster-Per-Tenant Multi-Tenancy
This approach provides each tenant with a dedicated Kubernetes cluster, offering the highest level of isolation.
Implementation Benefits:
- Maximum security and isolation boundaries
- Simplified compliance for regulated industries
- Independent cluster lifecycle management
- No resource contention between tenants
Operational Challenges:
- Higher infrastructure and management costs
- Complex cross-cluster networking and monitoring
- Increased operational overhead for platform teams
Best For: Enterprise customers with strict security requirements, regulated industries, and high-value tenants.
3. Virtual Cluster (vCluster) Architecture
Virtual clusters create lightweight, isolated Kubernetes environments within a host cluster, combining the benefits of both approaches.
Implementation Benefits:
- Strong isolation with cost efficiency
- Tenant-specific control planes and APIs
- Reduced infrastructure footprint
- Simplified tenant onboarding
Technical Challenges:
- More complex monitoring and troubleshooting
- Limited ecosystem tool compatibility
- Potential performance overhead
Best For: SaaS platforms, managed services, and organizations requiring strong isolation with cost constraints.
Critical Security Challenges in Multi-Tenant Kubernetes
Implementing secure multi-tenancy requires addressing several key security vectors:
Identity and Access Management (IAM)
Robust RBAC policies form the foundation of secure multi-tenancy. Key requirements include:
- Principle of Least Privilege: Grant minimum necessary permissions
- Namespace Scoping: Restrict access to tenant-specific resources
- Service Account Management: Implement automated credential rotation
- Audit Logging: Maintain comprehensive access logs for compliance
Network Security and Isolation
Network policies must prevent unauthorized cross-tenant communication:
# Example NetworkPolicy for tenant isolation
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: tenant-isolation
namespace: tenant-a
spec:
podSelector: {}
policyTypes:
- Ingress
- Egress
ingress:
- from:
- namespaceSelector:
matchLabels:
name: tenant-a
Resource Quotas and Limits
Prevent resource starvation and ensure fair usage through comprehensive quota management:
- CPU and Memory Limits: Per-namespace resource boundaries
- Storage Quotas: Persistent volume claim restrictions
- Object Count Limits: Pod, service, and ingress quotas
- Network Bandwidth: Traffic shaping and rate limiting
Data Security and Encryption
Protect tenant data through multiple encryption layers:
- Etcd Encryption: Encrypt data at rest in the Kubernetes datastore
- Secret Management: External secret stores (HashiCorp Vault, AWS Secrets Manager)
- Network Encryption: TLS for all inter-service communication
- Persistent Volume Encryption: Encrypted storage for stateful workloads
Observability in Multi-Tenant Kubernetes Environments
Effective monitoring and observability require tenant-aware tooling and data segregation strategies.
Metrics and Monitoring
Implement tenant-scoped monitoring with tools like:
- Prometheus: Multi-tenant federation with tenant-specific scrape configs
- Grafana: Tenant-isolated dashboards with data source segregation
- Alert Manager: Tenant-specific alerting rules and notification channels
Centralized Logging
Deploy logging solutions that maintain tenant boundaries:
- Fluentd/Fluent Bit: Tenant-aware log routing and filtering
- Elasticsearch/OpenSearch: Index-per-tenant data organization
- Log Aggregation: Centralized search with access controls
Distributed Tracing
Implement tracing solutions that respect tenant boundaries while enabling system-wide observability for platform teams.
The Stackgenie Approach to Multi-Tenant Kubernetes
At Stackgenie, we’ve refined our multi-tenancy implementation methodology through dozens of production deployments across diverse industries. Our approach focuses on three core principles: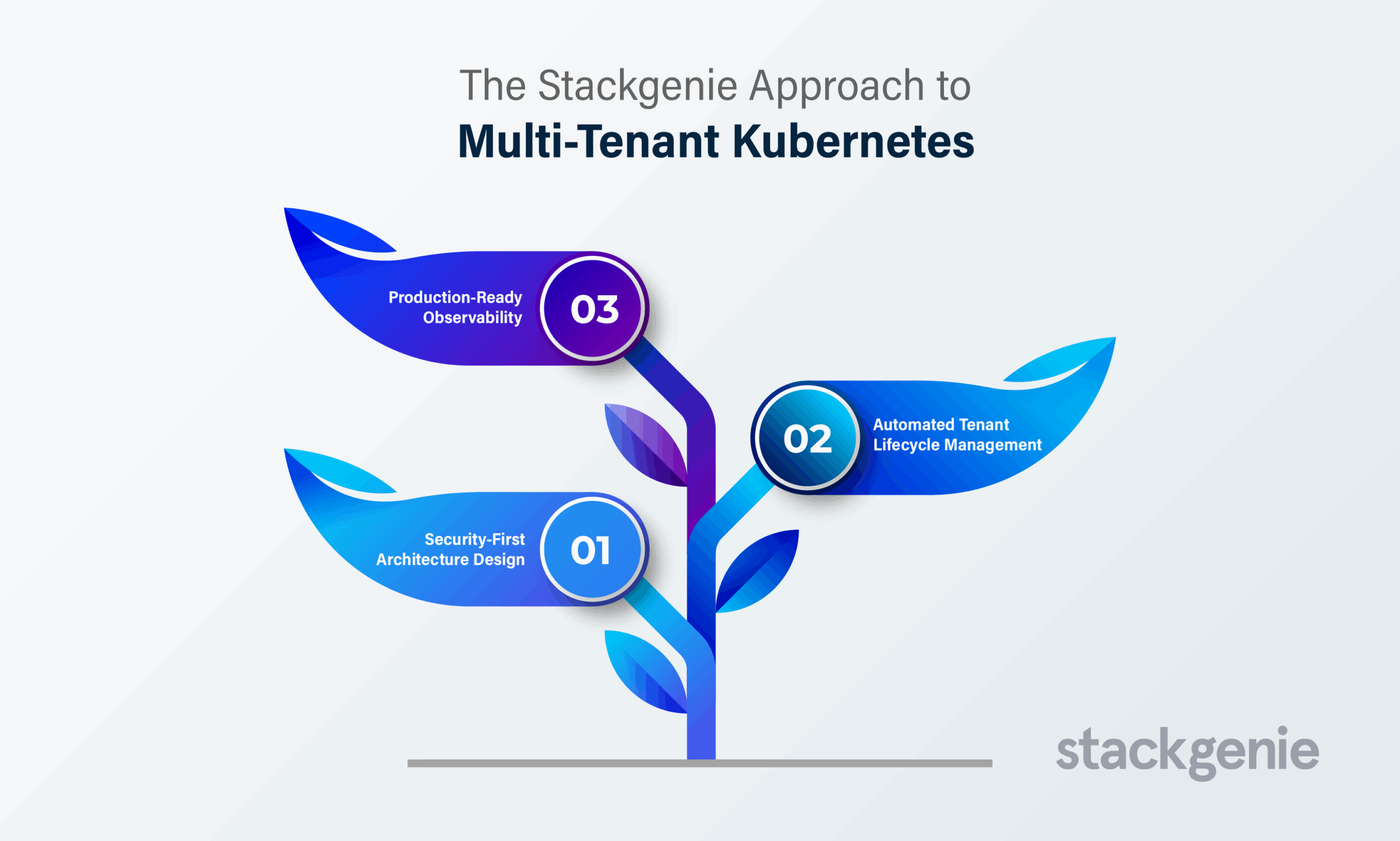
1. Security-First Architecture Design
We begin every multi-tenancy project with a comprehensive threat model, identifying potential attack vectors and implementing defense-in-depth strategies. Our security framework includes:
- Zero-Trust Networking: Default-deny policies with explicit allow rules
- Policy as Code: OPA Gatekeeper policies for automated compliance enforcement
- Continuous Security Scanning: Integrated vulnerability assessment and remediation
- Incident Response Planning: Tenant isolation procedures for security events
2. Automated Tenant Lifecycle Management
Manual tenant provisioning doesn’t scale. Our GitOps-based automation framework enables:
- Self-Service Provisioning: Developer-friendly tenant onboarding workflows
- Template-Driven Configuration: Consistent tenant environments with customization options
- Automated Compliance Checks: Policy validation before tenant activation
- Lifecycle Management: Automated scaling, backup, and decommissioning processes
3. Production-Ready Observability
Our monitoring stack provides comprehensive visibility while maintaining tenant isolation:
- Multi-Tenant Prometheus: Federated metrics collection with tenant labeling
- Grafana Dashboards: Role-based access to tenant-specific and cluster-wide metrics
- Centralized Logging: ELK stack with tenant-aware log segregation
- Custom Alerts: Tenant-specific alerting with escalation procedures
Real-World Case Study: SaaS Platform Multi-Tenancy
Challenge: A machine learning platform serving 200+ enterprise customers needed to consolidate infrastructure while maintaining strict data isolation and performance guarantees.
Solution: Stackgenie implemented a hybrid multi-tenancy model combining namespace-based isolation for development environments with dedicated node pools for production workloads.
Implementation Details:
- Tenant Onboarding: Automated provisioning through GitOps pipelines
- Security: OPA Gatekeeper policies enforcing data residency requirements
- Monitoring: Per-tenant Grafana dashboards with SLA tracking
- Cost Management: Detailed chargeback reporting by tenant
Results:
- 60% cost reduction through infrastructure consolidation
- 90% faster customer onboarding (minutes vs. days)
- Zero security incidents in 18 months of operation
- 99.9% uptime with tenant-isolated failure domains
Multi-Tenancy Best Practices and Implementation Guidelines
Security Best Practices
- Implement Defense in Depth: Layer security controls across network, compute, and data planes
- Regular Security Audits: Quarterly assessments of RBAC policies and network configurations
- Automated Policy Enforcement: Use admission controllers for consistent security posture
- Incident Response Planning: Develop tenant-specific containment procedures
Operational Excellence
- Infrastructure as Code: Version-controlled cluster and tenant configurations
- Automated Testing: Validate multi-tenancy isolation through chaos engineering
- Capacity Planning: Monitor resource utilization and plan for tenant growth
- Documentation: Maintain runbooks for common operational scenarios
Cost Optimization
- Resource Right-Sizing: Regular review and adjustment of tenant resource quotas
- Spot Instance Integration: Use preemptible instances for non-production workloads
- Storage Optimization: Implement lifecycle policies for persistent volumes
- Chargeback Mechanisms: Transparent cost allocation to business units
When to Choose Kubernetes Multi-Tenancy
Multi-tenancy isn’t appropriate for every organization. Consider this approach when you have:
Organizational Factors:
- Multiple development teams or business units
- SaaS products with numerous customers
- Regulatory requirements for resource sharing
Technical Requirements:
- Sufficient operational maturity for complex deployments
- Need for cost optimization through resource sharing
- Workloads with compatible resource profiles
Compliance Considerations:
- Acceptable risk profile for shared infrastructure
- Clear data classification and handling policies
- Audit and governance requirements
The Future of Kubernetes Multi-Tenancy
The Kubernetes ecosystem continues evolving to better support multi-tenant use cases:
Emerging Technologies:
- Hierarchical Namespaces: Better tenant organization and policy inheritance
- Virtual Kubelet: Serverless compute integration for tenant workloads
- Service Mesh Integration: Advanced traffic management and security policies
Industry Trends:
- GitOps Adoption: Declarative tenant management through Git workflows
- Policy as Code: Automated compliance through machine-readable policies
- Cloud Provider Integration: Managed multi-tenant Kubernetes services
Getting Started with Multi-Tenant Kubernetes
Ready to implement multi-tenancy in your Kubernetes environment? Here’s your roadmap:
Phase 1: Assessment and Planning (2-4 weeks)
- Inventory existing workloads and tenant requirements
- Define security and compliance requirements
- Choose appropriate multi-tenancy model
- Design tenant onboarding workflows
Phase 2: Implementation (4-8 weeks)
- Deploy security and policy enforcement tooling
- Implement automated tenant provisioning
- Configure monitoring and alerting systems
- Develop operational procedures
Phase 3: Migration and Optimization (4-12 weeks)
- Migrate existing workloads to multi-tenant architecture
- Optimize resource utilization and costs
- Train operations teams on new procedures
- Establish ongoing improvement processes
Conclusion: Scaling with Confidence Through Multi-Tenancy
Kubernetes multi-tenancy represents a powerful paradigm for organizations seeking to maximize infrastructure investments while maintaining security and operational excellence. Success requires careful planning, robust security implementation, and ongoing optimization—but the benefits of cost reduction, operational efficiency, and developer velocity make it a compelling choice for modern platform teams.
At Stackgenie, we’ve helped dozens of organizations successfully implement multi-tenant Kubernetes architectures, from startup SaaS platforms to Fortune 500 enterprises. Our proven methodology combines deep technical expertise with practical implementation experience to deliver production-ready solutions that scale with your business.
Whether you’re just beginning your multi-tenancy journey or looking to optimize an existing implementation, the right approach balances security, automation, and governance to enable confident scaling in your Kubernetes environment.
Ready to implement multi-tenancy in your Kubernetes environment? Contact us today for a consultation on architecting secure, scalable multi-tenant platforms that drive business value.